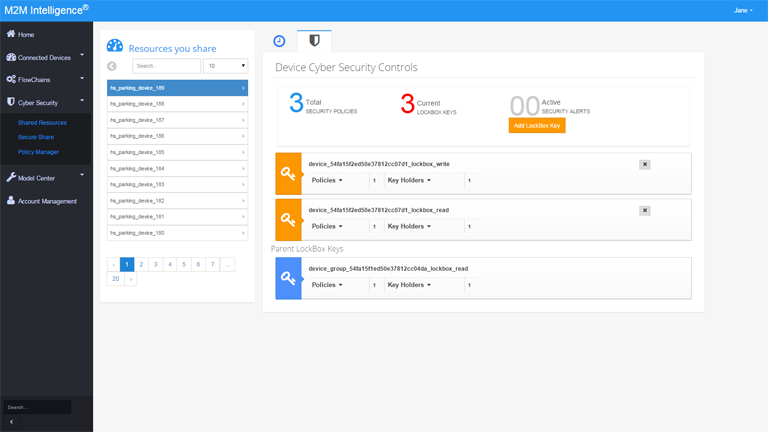
Lockbox
Enable secure sharing, multi-level privacy and control data access
The M2M & IoT ecosystem is a very diverse one – device manufacturers, telecoms, cloud providers, enterprises are just a few among them. Privacy becomes important when the data is being shared among the various constituents.
M2Mi's patented Lockbox security (US Patent 7,376,652) ensures multi-level privacy as well as controls each and every access to data thus ensuring data provenance, secure sharing with governance and compliance.